Computer/Digital Forensics-Analysis of Digital Evidence!
Computer/Digital Forensics-Analysis of Digital Evidence! The terms Computer Forensics and Digital Forensics are often used interchangeably. Technically, computer forensics refers to the investigation of computers. Digital Forensics refers to the investigation of ALL digital devices. In the real world, Digital Forensics is probably the more accurate name. Digital data storage is a component of almost all criminal activities investigations. Evidence is often hidden in computers, cell phones, flash drives, and even in cameras! Criminals are often painstaking in their data collection and record keeping. The criminals don’t seem to realize that keeping these records can ultimately help convict them!
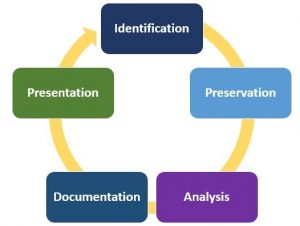
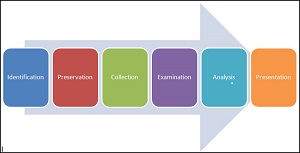
Computer/Digital Forensics-Analysis of Digital Evidence. The four steps of Digital Forensics are: preservation of evidence, collection of data from device, examination for irregularities, and analysis of the data and harvesting of evidence. When a search warrant is issued during an investigation, all digital devices are typically included in the warrant. These devices must be “photographed and preserved” as they were found when confiscated. It is the duty of the state to maintain the evidence in its original condition. Many digital devices allow “wireless access” to their data. The authorities must “preserve the evidence”. Digital evidence today is placed in a “Faraday Pouch or Container”. These Faraday pouches block wireless access to the data in the devices, preserving its integrity and preventing “electronic tampering” with evidence. Anyone and everyone who handles this evidence must be noted in a dated log. This log is called the COC/Chain of Custody” of the evidence.





Evidence Pouch→ Seized Device in Pouch→ Pouch Closed→ Secured-Pouch→ Pouch w/COC Log
Computer/Digital Forensics-Analysis of Digital Evidence. The digital information in devices is then “copied” by extracting the data to another disk. Analysis of this information is then performed. This involves looking for irregularities, artifacts, misnamed and hidden files, registry entries, emails, and protected files. An in-depth analysis of the data is performed and documented. When analysis is done properly, the evidence can be used in a court of law. Improper security and methods result in getting important evidence declared “inadmissible” in court!
V Technical Textiles, Inc. manufactures Faraday Pouches, bags, boxes for the safe transport/preservation of seized digital devices using conductive textiles. We can also design and provide RF Shielded lab boxes or workstations to facilitate the collection of data, examination of data, and analysis of data in a secure electronic environment. Please contact us to design the ideal Faraday Pouch for your specific evidentiary needs.
V Technical Textiles, Inc.
www.vtechtextiles.com
info@vtechtextiles.com
(315)-597-1674 Phone
(315)-597-6687 FAX



Experience, Research, Dedication, and Commitment











Leave a Reply