27Jul
02Jul
Nesting isn’t just for Birds, Nested Enclosures Help to Determine Shielding Effectiveness!
The determination of the Shielding Effectiveness (SE) of a material at high frequencies/small wavelengths can give large variations in results based on the testing method employed. One of the methods used to get more consistent results is to use a "nested" testing chamber, meaning a testing chamber is divided by a shielded wall across the middle of the chamber, with a window/hole in it. On the receiving side, there is no mode stirring and the antenna is set up to...
03Jan
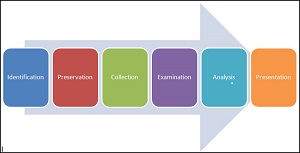
Digital Criminal Evidence-There is Proper Security Protocol for Keeping Digital Evidence Admissible in Court, Let Us Help You Handle Your Evidence Securely!
Despite the amazing amount of great evidentiary material that Forensic Sciences can provide, the care and treatment of evidence seized while in Law Enforcement custody can affect whether this persuasive information gathered through investigation will ever be presented in court or will be tossed out as "inadmissible in court". We all remember the O. J. Simpson trial, where "gold standard DNA evidence" was not allowed to be used as evidence in the trial due to a break in the "chain...
11Nov
Want to Protect Your Server System AND Cut Down on all the “Noise” in the Server Room? Put your Server in a Rack Cover!
When a company needs to protect its sensitive digital information, they improve their digital security by incorporating firewalls and virus scan programs into their network servers. This is smart practice by the network administrators, but today's criminal is always developing new techniques to steal digital information. By eavesdropping on the wireless signal of the servers, a "digital criminal" can access a company's most sensitive information. You store a lot of sensitive information in your Server or Blades. How are you going...
28Oct
RFID-It’s Not Just for Inventory Management Anymore!
RFID has been around since the end of World War II. One of the early uses of RFID was for inventory management. The inventory was accomplished by scanning the RFID Tag, the inventory was sent to the computer, logging in the presence of the item in the available inventory. There are two different forms of RFID Tags, each based on how the information from the RFID Tag is transmitted to the scanner. A "passive RFID Tag" means that the tag is...
28May